What's happened?
- A malware variant titled the GootKit Loader or Gootloader is actively targeting Australian healthcare organisations.
- Using a tactic known as ‘search engine optimisation poisoning’, cybercriminals are hosting malware on compromised websites that are designed to look like forum posts. See sample images below:
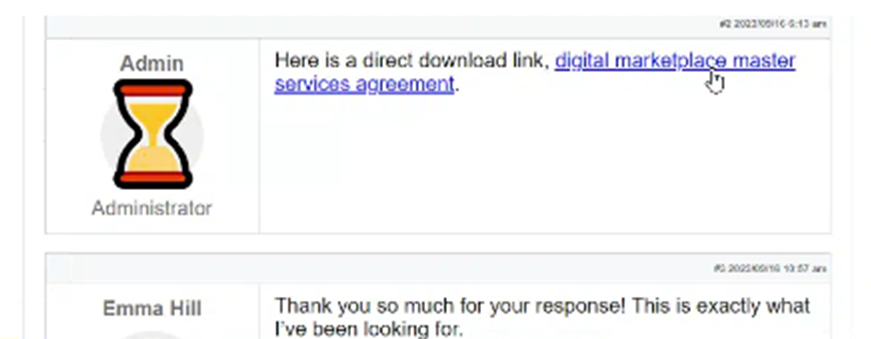
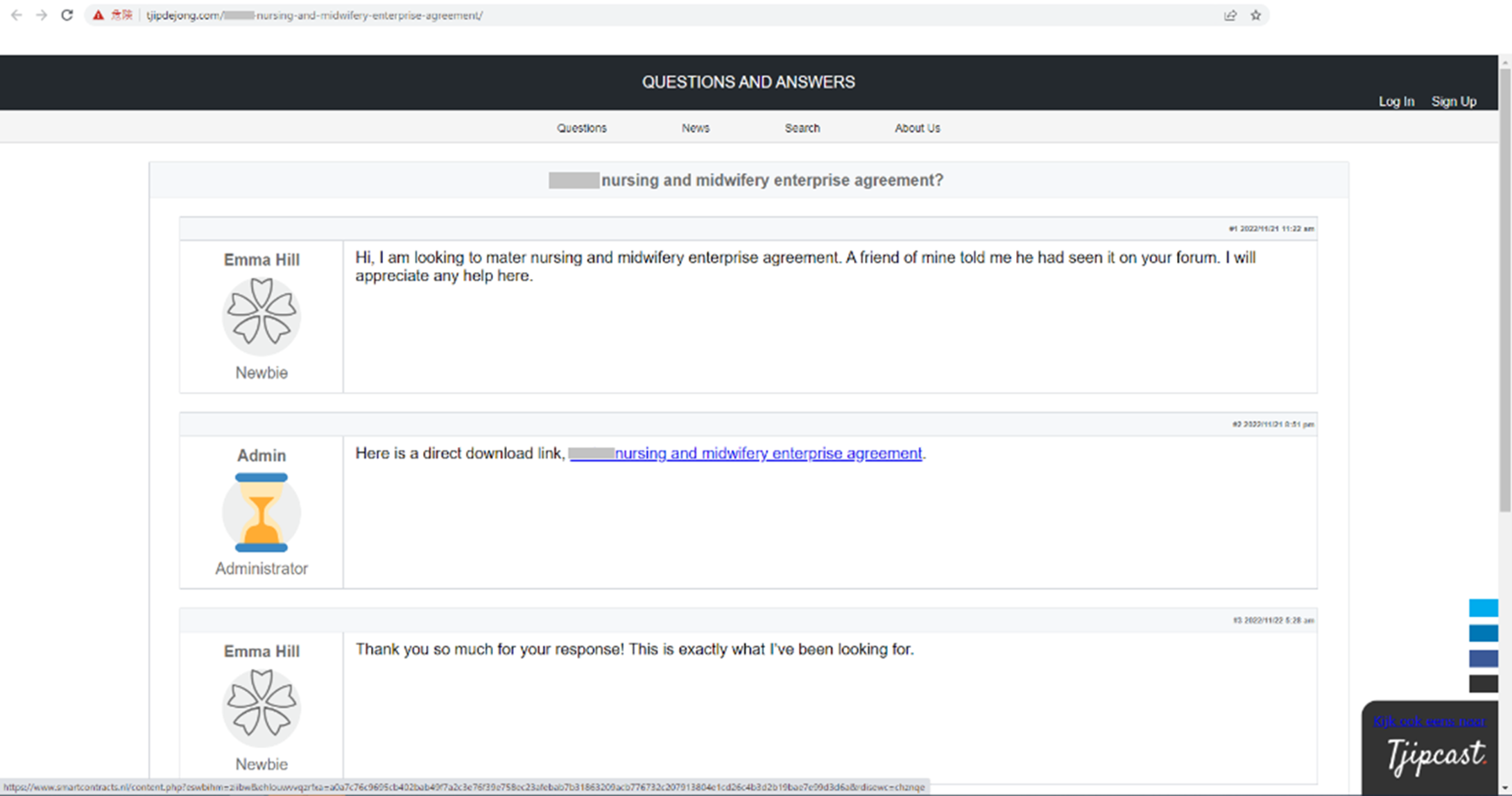
- Search engine optimisation poisoning is a tactic that cybercriminals employ, creating many posts on many legitimate sites that include links to the threat actor's websites
- This attack is a concern as it relies on the user to Google search keywords that are of relevant interest. For example, terms such as digital services, master agreement, agreement, hospital, health, and medical. Australian cities have also been cited.
How could this impact me?
- The GootLoader malware is used to infiltrate an organisation’s network to steal valuable data, and establish a backdoor for the attacker to install further malware such as ransomware.
- This can lead to disruption of an organisation’s systems or result in the theft of information that is of value. Attackers may exploit the access or sell access to another criminal group.
What do I need to do?
- Notify your staff of the ongoing campaign. Ensure they are aware of the indicators of a malicious GootLoader website, such as an incorrect or suspicious website domain name.
- Never open website links or attachments on a malicious website. Staff looking for official documents should download content from the authoritative source or consult internally.
- If a suspected GootLoader infection occurs, ensure all infected devices are isolated immediately and reimaged to prevent further spread.
If your organisation has been affected and your organisation has access to the My Health Record system, please inform the Australian Digital Health Agency immediately at the email address listed at the end of this email.
Where can I get more information?
For more information visit:
